Cyber Essentials Version 3.1 – Everything You Need To Know About The Update
Posted on: 3rd July 2023
April this year saw the latest updates to the government approved Cyber Essentials scheme, which includes five technical controls that help protect organisations of all sizes from the majority of commodity cyber-attacks. The Cyber Essentials certification badge signals to customers, investors and those in the supply chain that an organisation has put the government approved minimum level of cyber security in place and can be trusted with their data and business.
A team of experts review the scheme at regular intervals to ensure it stays effective in the ever-evolving threat landscape, and allows UK businesses to continue raising the bar for their cyber security.
Cyber Essentials 3.1 has some important guidance and clarifications that organisations need to be aware of, and our Head of Cyber Security Simon Hopkin takes a look at what the changes mean.
The updates were made in response to feedback from assessors and applicants, and in a bid to make the process more user-friendly and accessible, new features will include more guidance documents for applications, including help understanding the questions, plus access to a wide-ranging knowledge base.
The changes came into effect on 24th April 2023 and all applications started after this date will use the new requirements, and the Montpellier question set will replace the previous Evendine question set. The grace periods for some of the requirements from the 2022 update ended on 24th April.
Cyber Essentials Montpellier Update Explained
1. Updated definition of ‘software’ to clarify where firmware is in scope
The definition has been updated as follows: Software includes operating systems, commercial off-the-shelf applications, plugins, interpreters, scripts, libraries, network software and firewall and router firmware. Organisations will be required to provide the make and model of firmware devices, which will enable certification bodies to determine if they are still receiving security updates. The reason for this change is that firewall and router firmware acts as the operating system of these devices – keeping them up to date is extremely important from a security perspective.
2. A greater emphasis on asset management
This means as an organisation you need to establish and maintain a resource that contains accurate information about any devices within the business. Asset management is a fundamental control that can help your organisation meet the requirements for Cyber Essentials certification. Good asset management will help track and control devices as they’re introduced to your business, allowing you to quickly discover any unsupported/out-of-date assets.
3. BYOD (Bring Your Own Device) Guidance
The Cyber Essentials standard now provides further information and advice on the use of BYOD, please see the NCSC’s guidance.
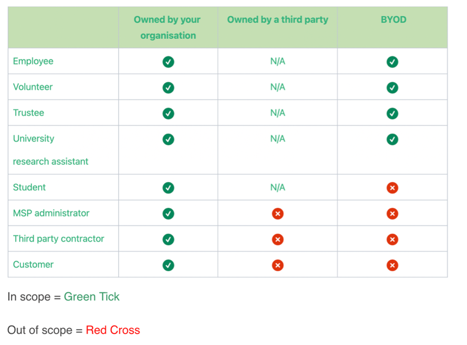
4. Clarification on third party devices
The standard requires that all end user devices that your organisation owns and that are loaned to a third party must be included in the assessment scope. IASME has created the following table to provide clarity:
5. Updated ‘Device unlocking’ section to accommodate vendor restrictions
‘Device unlocking’ has been updated to reflect that some configurations can’t be altered because of vendor restrictions. Many smartphones have built in “lock-out” timers that cannot be changed. It is acceptable that you go with the minimum number of sign-in attempts allowed by the device before locking. For example, Samsung have set their minimum sign-in attempts at 15, this is not alterable. This is considered acceptable within the Cyber Essentials framework.
6. Updated ‘Malware protection’ section
The ‘Malware protection’ section has been updated. In line with research and recommendations from vendors this section has been updated. Any anti-malware software must be updated in line with vendor requirements, prevent malware from running, prevent execution of malicious code and prevent connections to malicious websites over the internet. Application Allow listing also falls under this category. Only approved applications are allowed to execute on devices. They must be approved before being deployed, and you should maintain a list of approved applications for Cyber Essentials certification.
7. Zero trust architecture guidance
Network architecture is changing. More services are moving to the cloud and use of Software as a Service (SaaS) continues to grow. At the same time, many organisations are embracing flexible working, which means lots of different device types may connect to your systems from many locations. It’s also increasingly common for organisations to share data with their partners and guest users, which requires more granular access control policies.
Zero trust architecture is designed to cope with these changing conditions by enabling an improved user experience for remote access and data sharing. A zero-trust architecture is an approach to system design where inherent trust in the network is removed. Instead, the network is assumed hostile, and each access request is verified, based on an access policy. Confidence in a request is achieved by building context, which relies on strong authentication, authorisation, device health, and the value of the data being accessed.
NCSC and IASME have considered the alignment of Cyber Essentials with the zero trust architecture models. They are confident that implementing the Cyber Essentials technical controls does not prevent you from using a zero-trust architecture as defined by the NCSC guidance.
General usability changes include:
The specification document for Cyber Essentials Plus has been updated and is now active.
Document Readability (Style and language adjustments).
The Cyber Essentials scheme requirements are now a consistent order: firewalls, secure configuration, security update management, user access controls, and malware protection.
Please consider that with these changes, there is likely to be an increase in the duration of the Cyber Essentials certification process.
So what does all this mean for you?
If your application started on or after 24th April you will need to meet the requirements of Cyber Essentials 3.1. For those organisations who already hold Cyber Essentials, the changes only come into effect at your annual renewal, and as usual, we will be in touch at least three months prior to that to help you make sure you are prepared.
If you have any queries or concerns meanwhile, please do speak to your ITPS account manager. There is also an updated set of FAQs on the NCSC website which you may find useful.
For more information on any of our expert cyber security solutions for your business, please contact us.